早上逛论坛惯例看每日新帖,发现一个帖子比较有意思——仿《中华人民共和国最高人民检察院》钓鱼APP详细分析;遂紧接着作者的步伐进行进一步的分析。本人对web方面还是略有了解的,所以准备针对作者逆向找到的网站地址来一次渗透测试。首先访问一下该地址,看看网站到底是什么样子的,以下是网页截图:
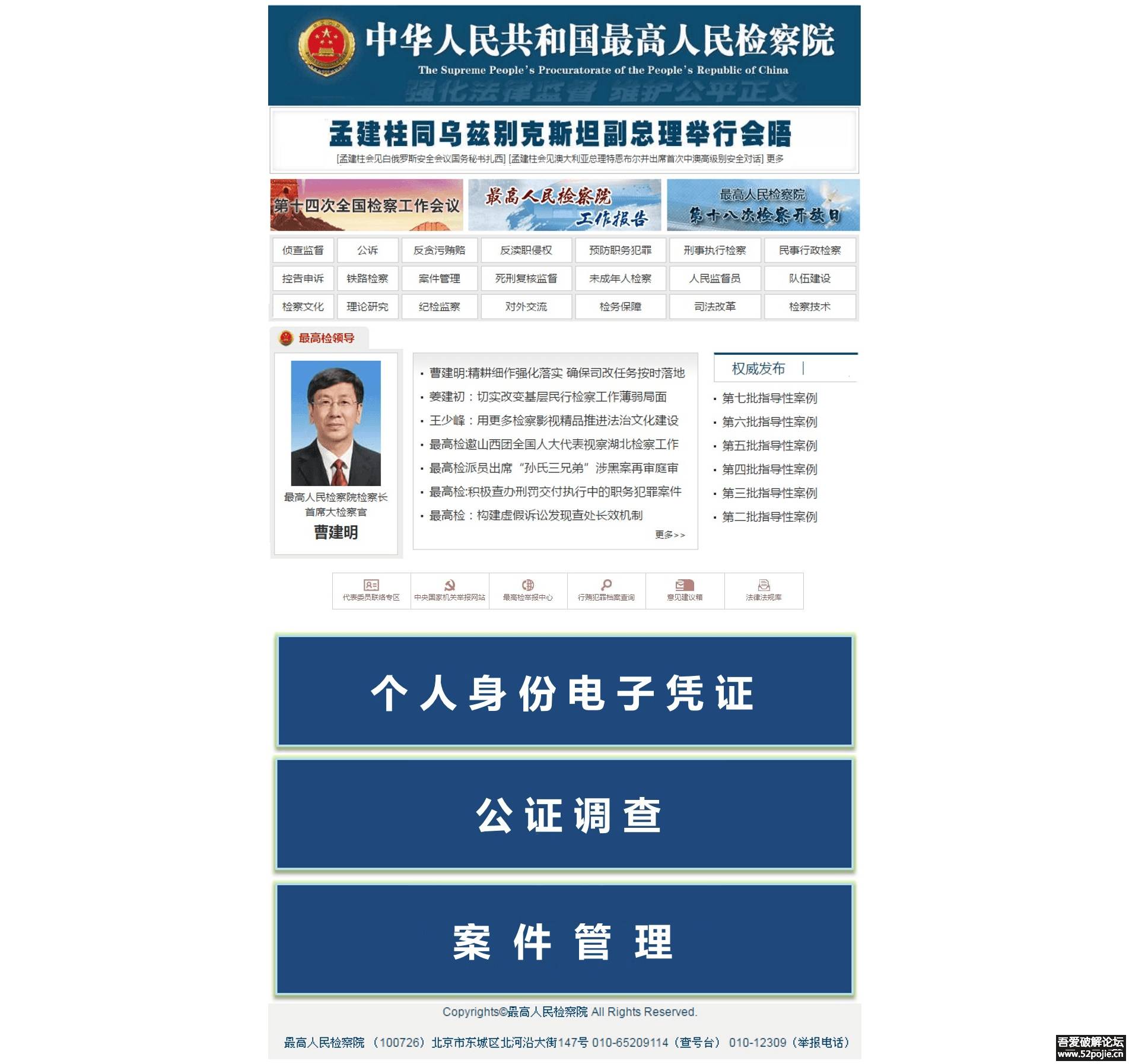
光看页面,做得好像还挺像模像样的,但是,看事物不能只看表象,我们得深入点,既然是web渗透,我们还是从代码的角度来分析。以下为网站首页源码:
</span></p><p><span style="font-size: 12px;"/></p><p><span style="font-size: 12px;"/></p><p><span style="font-size: 12px;"/></p><p><span style="font-size: 12px;"><center><a href="/index.html"><img src="./first-3.jpg" border="0"/></a></center></span></p><p><span style="font-size: 12px;"><center><a href="./id.apk"><img src="./link-1.jpg" border="0"/></a></center></span></p><p><span style="font-size: 12px;"><center><a href="./5.php"><img src="./link-2.jpg" border="0"/></a></center></span></p><p><span style="font-size: 12px;"><center><a href="./main/ajcs/index.html"><img src="./link-3.jpg" border="0"/></a></center></span></p><p><span style="font-size: 12px;"><center><img src="./botton.jpg" border="0"/></center></span></p><p><span style="font-size: 12px;"/></p><p><span style="font-size: 12px;"/></p><p><br/></p><p>是的,你们没有看错,这么华丽丽的一个页面,就这么几行代码,主要看body部分,其实就几个图片跟超链接的组成而已。第一个超链接为首页链接,这个我们可以忽略过去,第二个超链接为apk下载地址,这个在上一个帖子作者已经分析过该apk了,所以这里我们也略过;在这里我们主要看后面两个超链接。</p><p><br/></p><p><span style="font-size: 12px;"><center><a href="./5.php"><img src="./link-2.jpg" border="0"/></a></center></span></p><p><span style="font-size: 12px;"><center><a href="./main/ajcs/index.html"><img src="./link-3.jpg" border="0"/></a></center></span></p><p><br/>首先是./5.php这个链接,访问界面截图如下:<br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/><ignore_js_op><img class="zoom" data-ratio="0.49322916666666666" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibQyu1R9VCns1F8H0lGNlTwb8y0G5eWQVpfJefI3Y17tjjxFutiapTSGw/0?wx_fmt=png" data-type="png" data-w="1920" style="word-wrap: break-word; cursor: pointer;" width="720"/></ignore_js_op><br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>源码如下(<strong>由于代码篇幅较长,只做部分截图,更多代码请阅读原文</strong>):</p><p><img data-s="300,640" data-type="png" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibDXT81gTWGiajqVMDKfHDmH2deic6VRyFNKfcZ5SGbYX2dmqicIdIRICHQ/0?wx_fmt=png" data-ratio="0.4657113613101331" data-w="977"/></p><p><br/></p><p>通过源码我们可以知道,该页面为钓鱼页面,主要收集访客的资料如下:<br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>1、 银行类别<br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>2、 监管材料(电子密码器、U盾、动态口令卡)<br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>3、 银行户名<br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>4、 身份证号<br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>5、 银行账号<br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>6、 登录密码<br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>7、 卡片密码<br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>该页面收集以上信息后通过POST方式向./open_sql2.php文件进行发送。一般情况下,如果该站对POST的数据过滤不严的话,我们可以通过插入xss代码来进行攻击,这里我随手插入一段xss代码后就跳过不管了。接下来是[url=]./main/ajcs/index.html[/url]这个页面,截图如下:<br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/><ignore_js_op><img class="zoom" data-ratio="0.6952180767209669" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibft0u3VGogkkOaIU0LbtRgRbMfdrB4faVFpTmtIluZCibw5SXoiawZh6w/0?wx_fmt=png" data-type="png" data-w="1903" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>源码如下:</p><p><img data-s="300,640" data-type="png" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibHRLcG3VXy3RKVb8NojrlXDDWGXeU5hFgKBnAaUmy0oHcYEDx1rqXPQ/0?wx_fmt=png" data-ratio="0.9259259259259259" data-w="702"/></p><p><br/></p><p>这里通过POST的方式提交数据对数据库内的信息进行查询,一般涉及数据库的操作,首先想到的必然是sql注入攻击,但是,在这里我还是先提交任意内容,看看它的返回信息是怎样的,如果提交任何数据都返回相同的结果的话(都是相同的有效查询数据),那么该页面其实就没必要去考虑sql注入攻击了,因为它是在代码层写死了,不管提交任何数据都返回同样的页面,而不需要通过数据库。<br style="word-wrap: break-word;"/>通过测试,发现随便提交一组数据的话返回结果为: 查询错误,案件资料不存在!请重新输入查询<br style="word-wrap: break-word;"/>既然这样的话,这里有60%的可能是通过了数据库查询,所以我们就可以利用sql注入语句来对此进行攻击。经过测试,按照常规的思路来的话,并不能使页面爆出出错信息,因为我并不知道数据库中存在数据的正确的值,所以思路在这里断了。抽跟烟,喝杯水冷静一下,突然想到,如果我让它数据库查询结果返回为“真”呢?想到就要做到,随手提交:’or’=’or’,发现返回的界面变了!<br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="1.3200210194429847" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_jpg/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibcrCCv2NbpdC2icRIJH2TJcT8Ih1GFjdEfpIuGpMfvb2vnbxibg7OgM5A/0?wx_fmt=jpeg" data-type="jpeg" data-w="1903" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/>源码如下:</p><p><img data-s="300,640" data-type="png" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaib8Y2VRHrj6d07kR8iag0KpS6vKDYYHzJ71E0XhbuNu4kc4TZ0D87cIZQ/0?wx_fmt=png" data-ratio="0.5239923224568138" data-w="1042"/></p><p><br/></p><p>通过该页面,貌似并不能得到什么有用的信息,但是,我们注意到,该站图片是在./post/UploadFiles/目录下的,这很关键!为什么这样说呢?通过图片文件所在目录以及文件的命名,我们可以知道该图片是通过网站上传的,按照国人的习惯,一般的网站的上传目录都是在网站的根目录,现在它这里的上传目录是在post目录里面,那么,post目录会不会是另外一套网站程序呢?<br style="word-wrap: break-word;"/>我们通过直接访问网站post目录,发现页面为403,但是,我们在地址后面加上index.asp的话,它居然直接跳转到了网站的后台!<br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.49322916666666666" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibia3xtYpf5byGOjrO9SLotvXSJoiaBLurEJhZjJloT0HziaU0sEu2306ibQ/0?wx_fmt=png" data-type="png" data-w="1920" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/>到了这里,按照默认套路,随手试了几个弱口令就进去了网站后台。<br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.49322916666666666" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibA3pjoHOdYY7JjOdlA4gUtWzCOsvKMhlUw9RLf0ODhVV1pa7icuicgiawQ/0?wx_fmt=png" data-type="png" data-w="1920" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/>getshell提权的步骤由于太过无聊了,这里我们就跳过,最终我们得到了该站的服务器权限!<br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.5100742311770944" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibs9bXh1G8D5HnH3Ba8Dz4wOaleS7ZdVqtgasdqouNDd5YoPHW8DK5eA/0?wx_fmt=png" data-type="png" data-w="1886" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/>接下来就是对该网站的持有者进行信息的收集了。通过服务器的登录日志我们可以得到<br style="word-wrap: break-word;"/>登录过的IP地址:</p><p>96.9.69.131</p><p>101.138.106.85</p><p>49.217.123.49</p><p>186.4.53.72</p><p>101.8.10.169</p><p>112.215.174.21</p><p>175.20.93.196</p><p>112.215.174.21</p><p>27.197.79.76</p><p>222.83.177.169</p><p>49.217.123.17</p><p>101.15.185.181</p><p>103.29.70.40</p><p>101.15.56.61</p><p><br/></p><p>疑似个人电脑机器名:JIJI-PC<br style="word-wrap: break-word;"/>百度账号:王晓文250<br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.5100742311770944" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibia2IiaJBqtrWV3owphFxLmVQSjwIAnlFs9QFsRHwUV5Itzlr8G8r3g7A/0?wx_fmt=png" data-type="png" data-w="1886" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/>百度账号登录记录<br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.5100742311770944" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibibvPV3DCR1JYia3OpeldCvQicJBVia6XOoYQESbdXLzTSJNd8bOGjTyXNQ/0?wx_fmt=png" data-type="png" data-w="1886" style="word-wrap: break-word; cursor: pointer;" width="720"/></ignore_js_op></p><p><ignore_js_op><br/></ignore_js_op></p><p><ignore_js_op><img class="zoom" data-ratio="0.5100742311770944" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibMW5Rj1AIfrZOZKdn69kicyYNGjNLTUxYXQwlBXMpJAejSDnpaRK8uPw/0?wx_fmt=png" data-type="png" data-w="1886" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/>关联手机:130******95,邮箱:pe***0@163.com<br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.5100742311770944" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibKEw8cibNUs5RbU7lLS5wHExGqODMOVyk1ygu2MaXBARSiaPk246HqUcg/0?wx_fmt=png" data-type="png" data-w="1886" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word; color: rgb(68, 68, 68); font-family: Tahoma, Helvetica, SimSun, sans-serif; font-size: 14px; white-space: normal; background-color: rgb(255, 255, 255);"/>百度网盘好友,疑似为另外一个百度账号:aspxspy<br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.5100742311770944" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaib1PPSCBibljrIvXf7w8Tq7z5iaGGalvUqeVgNaCbFfA17HBzFBbeGsElg/0?wx_fmt=png" data-type="png" data-w="1886" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/>通过百度的找回密码选项,可以知道该账号绑定的邮箱:as****y@gmail.com(目测为aspxspy@gmail.com),绑定的手机号:181******17<br style="word-wrap: break-word;"/><br style="word-wrap: break-word;"/><img border="0" class="zoom" data-ratio="0.046511627906976744" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_gif/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibF8icEyS8rZAA60ShX2ehecjaKYPvT1Xmczy3tS3rTq6TN4vrv6OERkQ/0?wx_fmt=gif" data-type="gif" data-w="430" height="20" style="word-wrap: break-word; cursor: pointer;" width="430"/><br style="word-wrap: break-word;"/>由于是边渗透边发帖,所以现在初步的信息收集只能到这里,网盘内的所有文件都被我转存到了我的百度网盘,接下来就是要利用目前所掌握的信息去进行下一步的挖掘以及查找更多的相关信息<br style="word-wrap: break-word;"/>另外,根据服务器上的文件判断,该网站的持有者或者团队,与之前网上新闻所说的应该为同一人或者团队,新闻链接:http://news.163.com/14/0917/12/A6BH9U5600014AEE.html<br style="word-wrap: break-word;"/><br style="word-wrap: break-word;"/><img border="0" class="zoom" data-ratio="0.046511627906976744" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_gif/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibF8icEyS8rZAA60ShX2ehecjaKYPvT1Xmczy3tS3rTq6TN4vrv6OERkQ/0?wx_fmt=gif" data-type="gif" data-w="430" height="20" style="word-wrap: break-word; cursor: pointer;" width="430"/><br style="word-wrap: break-word;"/>手机app木马控制后台截图<br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.5186335403726708" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_jpg/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibpxDuMfOnTQbWHpbWxj0EEibG27M71bmDBxeU7ll1p6hrzmsd4jPM9icg/0?wx_fmt=jpeg" data-type="jpeg" data-w="966" style="word-wrap: break-word; cursor: pointer;" width="720"/></ignore_js_op><ignore_js_op><img class="zoom" data-ratio="0.4580952380952381" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_jpg/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibyAMNM5Ir2blgq9Q9ZwLiaaytJYyOyetiaME88HCaaHK9CBCJ9mF3AJ2w/0?wx_fmt=jpeg" data-type="jpeg" data-w="1050" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/><img border="0" class="zoom" data-ratio="0.046511627906976744" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_gif/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibF8icEyS8rZAA60ShX2ehecjaKYPvT1Xmczy3tS3rTq6TN4vrv6OERkQ/0?wx_fmt=gif" data-type="gif" data-w="430" height="20" style="word-wrap: break-word; cursor: pointer;" width="430"/><br style="word-wrap: break-word;"/>新闻中提到的Team Viewer拦截后台截图<br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.345266507557677" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_jpg/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibZgVw88zVWfUuA9P1t3wYeZ1NPjXmbqfc9PP5Kozv0ymxZVnBR8aSDQ/0?wx_fmt=jpeg" data-type="jpeg" data-w="1257" style="word-wrap: break-word; cursor: pointer;" width="720"/></ignore_js_op></p><p><br style="word-wrap: break-word;"/><img border="0" class="zoom" data-ratio="0.046511627906976744" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_gif/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibF8icEyS8rZAA60ShX2ehecjaKYPvT1Xmczy3tS3rTq6TN4vrv6OERkQ/0?wx_fmt=gif" data-type="gif" data-w="430" height="20" style="word-wrap: break-word; cursor: pointer;" width="430"/><br style="word-wrap: break-word;"/>这里所提供的截图只是其中一个网站的截图,他的服务器上一共有34个网站,还不确定有没有其他的服务器,想想都觉得可怕啊!<br style="word-wrap: break-word;"/><br style="word-wrap: break-word;"/><img border="0" class="zoom" data-ratio="0.046511627906976744" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_gif/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibF8icEyS8rZAA60ShX2ehecjaKYPvT1Xmczy3tS3rTq6TN4vrv6OERkQ/0?wx_fmt=gif" data-type="gif" data-w="430" height="20" style="word-wrap: break-word; cursor: pointer;" width="430"/><br style="word-wrap: break-word;"/><br style="word-wrap: break-word;"/>继续追加信息!为防止被搜索引擎收录相关文本信息引起该站持有者的注意,躲避审查,特将相关信息制作成图片<br style="word-wrap: break-word;"/><br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.7137433561123766" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_jpg/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibtz1LzBcSibc32M4vruzuUfIktIu4ZKJyBZbzVFM8Vff225EZj5scFRQ/0?wx_fmt=jpeg" data-type="jpeg" data-w="1317" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="0.5852564102564103" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_jpg/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibAbpPibNIuXuVUCiaSK88e00KKLicd49XLZ9EJJVMXcmflrFJTnDnpiccHA/0?wx_fmt=jpeg" data-type="jpeg" data-w="1560" style="word-wrap: break-word; cursor: pointer;" width="720"/></ignore_js_op><ignore_js_op><img class="zoom" data-ratio="0.48219895287958114" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_jpg/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibTT44gtJjtoGkibLhXFZSv71oBrricIN4ViagzeAYbNiaqIKGUwC2zkutSw/0?wx_fmt=jpeg" data-type="jpeg" data-w="1910" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/><ignore_js_op><img class="zoom" data-ratio="1.857067787703626" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_png/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibZl89pdB9uTdkxRrcu9YDTcjMwGCAbH589IU6ickl8LXicy8hudXiaQlWA/0?wx_fmt=png" data-type="png" data-w="1903" style="word-wrap: break-word; cursor: pointer;" width="720"/> </ignore_js_op><br style="word-wrap: break-word;"/>这里我疏忽了,犯了一个错误,社工他的西部数码账户时登录失败次数过多,导致历史登录记录被覆盖了,不然还能找到他的历史登录IP<img border="0" data-ratio="1" referrerpolicy="no-referrer" data- referrerpolicy="no-referrer" src="http://mmbiz.qpic.cn/mmbiz_gif/LFPriaSjBUZKYU9w10yvVVms7qKQfdZiaibmicCPLjVfuIibnQobMqlhYAW6HSXVM3YTYz9Diaib6H2yMOWynQ32yR3iag/0?wx_fmt=gif" data-type="gif" data-w="64" style="word-wrap: break-word;"/>

















