前言
实战中,当通过某种方式拿下测试虚拟机权限时,发现该机器可出网。此时为了内网横向渗透与团队间的协同作战,可以利用Frp在该机器与VPS之间建立一条“专属通道”,并借助这条通道达到内网穿透的效果。实战中更多时候依靠 Socks5 。
更多详细使用方法,可查看官方Github,这里不再赘述。
https://github.com/fatedier/frp/
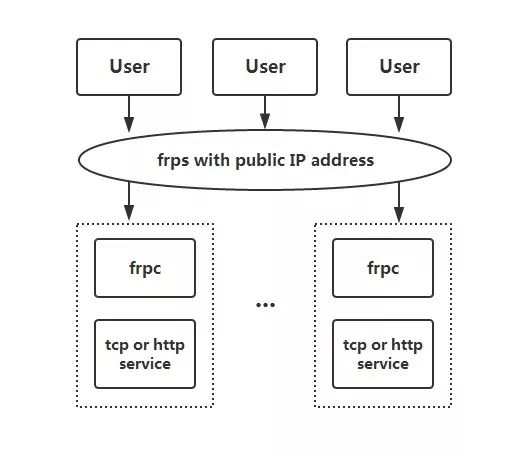
前期准备
先准备一台VPS与域名。
因某种情况会更换VPS地址,为了减少更改frp配置文件的次数,所以做域名泛解析。若更换VPS,直接编辑域名解析地址即可。

下载地址
Frp下载地址 [跨平台,实战中根据目标机版本选择下载]
https://github.com/fatedier/frp/releases
配置文件
服务端
1
|
|
2
|
[common]
|
3
|
|
4
|
bind_addr = 0.0.0.0
|
5
|
|
6
|
bind_port = 7007
|
7
|
|
8
|
|
9
|
dashboard_port = 6609
|
10
|
|
11
|
dashboard_user = SuperMan
|
12
|
dashboard_pwd = WC3pvjmh2tt8
|
13
|
|
14
|
|
15
|
log_file = ./frps.log
|
16
|
|
17
|
log_level = info
|
18
|
|
19
|
log_max_days = 3
|
20
|
|
21
|
|
22
|
auth_token = E0iQEBOdoJeh
|
23
|
|
24
|
privilege_mode = true
|
25
|
|
26
|
privilege_token = kukezkHC8R1H
|
27
|
|
28
|
privilege_allow_ports = 4000-50000
|
29
|
|
30
|
|
31
|
heartbeat_timeout = 30
|
32
|
|
33
|
|
34
|
max_pool_count = 20
|
35
|
|
36
|
|
37
|
authentication_timeout = 900
|
38
|
|
39
|
|
40
|
subdomain_host = xxxx.online
|
客户端
1
|
|
2
|
[common]
|
3
|
|
4
|
server_addr = frp.xxxx.online
|
5
|
|
6
|
server_port = 7007
|
7
|
|
8
|
|
9
|
auth_token = E0iQEBOdoJeh
|
10
|
|
11
|
privilege_mode = true
|
12
|
|
13
|
privilege_token = kukezkHC8R1H
|
14
|
|
15
|
|
16
|
heartbeat_interval = 10
|
17
|
heartbeat_timeout = 30
|
18
|
|
19
|
|
20
|
use_encryption = true
|
21
|
|
22
|
use_compression = true
|
23
|
|
24
|
|
25
|
pool_count = 20
|
26
|
|
27
|
|
28
|
[socks5]
|
29
|
type = tcp
|
30
|
|
31
|
remote_port = 9066
|
32
|
|
33
|
plugin = socks5
|
34
|
|
35
|
|















