目标:让libhasp_android_xxx.so能加载自己的id_xxx.so
工具:IDA,python
主要是对某safe加密锁的android保护库的补丁工具,最开始是手动修改代码,极不方便。有了这个脚本工具可一键生成补丁,轻松自在。
先用IDA加载libhasp_android_x.so大概分析一下,下面是导出函数表
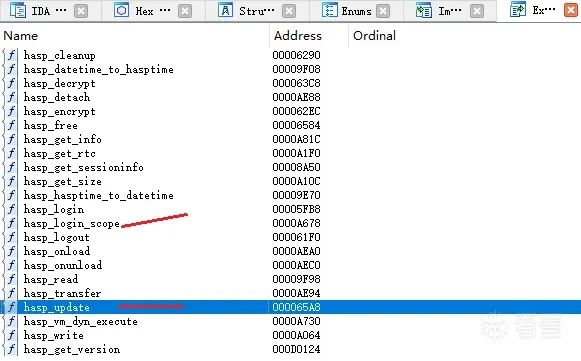
实际要操作的就两函数,一个是 hasp_login_scope,另外一个是 hasp_update.因为hasp_update一般程序中用不到,所以会把补丁代码放到这部分。双击hasp_login_scope进入,会看到函数的前面有些空调函数可以利用,nullsub我为了好记就叫他空调函数吧。
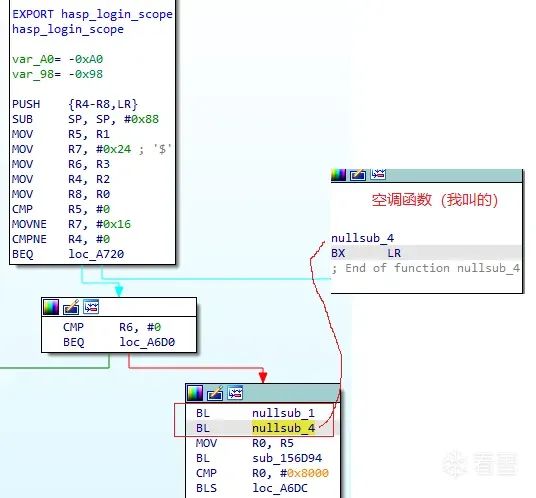
以后脚本会把 BL nullsub_4(nullsub_1也行)也成BL hasp_update,这样当程序调用加密锁时(一般第一就是hasp_login_scope)就会先来到hasp_update,下一步修改hasp_update字节,实现dlopen加载另外一个so。
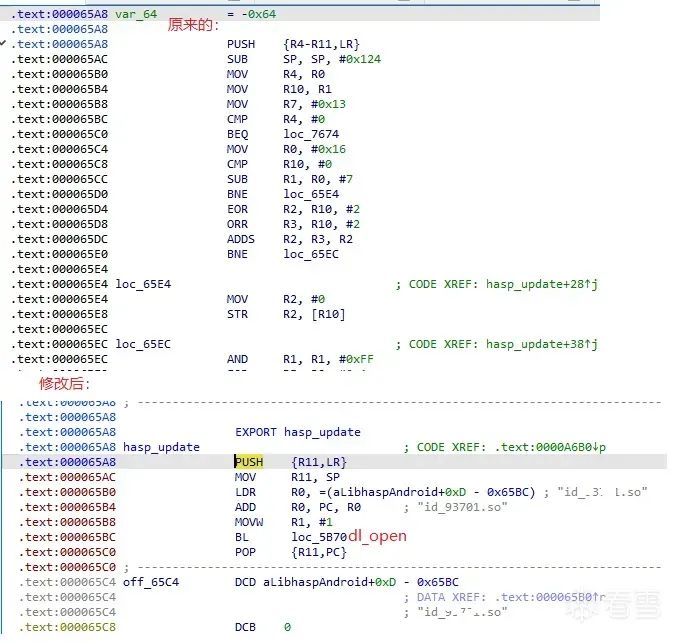
![export ]
修改后的hasp_update里用到的字符串,和dlopen是需要重定位,要修正地址的,手动修改比较麻烦,有计算公式可自行bing chat,有了脚本就省事多了。其实脚本也参考bing AI. AI真是个宝!
再来看看原dlopen的地址:
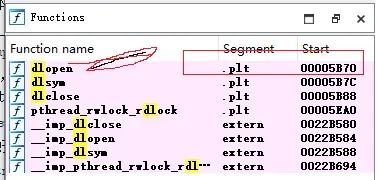
脚本上要用到dlopen,hasp_login_scope,及hasp_update的地址,还是给出脚本脚本,然后你找一个合适的so去研究吧。其它linux类的都可以这样做加载补丁,可研究修改。
import logging
from elftools.elf.elffile import ELFFile
plt_dlopen_of = 0x00007264
plt_dlopen_of = 0x00005B70
hasp_login_scope_BL = 0xA6B0
FileOrg = "libhasp_android_xxxx.so"
FileNew = FileOrg + ".new"
hasp_update_of = 0x00000000
FileNameAdd = 0x00000000
hasp_update_code_new = b'\x00\x48\x2D\xE9\x0D\xB0\xA0\xE1\x0C\x00\x9F\xE5\x00\x00\x8F\xE0\x01\x10\x00\xE3\x1C\x00\x00\xEB\x00\x88\xBD\xE8\xEA\xFC\xFF\xFF'
logging.basicConfig(
filename='AutoFixSo.log',
filemode='w',
format='%(asctime)s - %(levelname)s - %(message)s',
datefmt='%Y-%m-%d %H:%M:%S',
level=logging.DEBUG
)
def find_string_offset(binary_file, search_string):
with open(binary_file, 'rb') as f:
data = f.read()
index = data.find(search_string.encode())
if index != -1:
print(f"Found '{search_string}' at offset 0x{index:X}")
return index
else:
print(f"String '{search_string}' not found in the binary file.")
return -1
FileNameAdd = find_string_offset(FileOrg,FileOrg)
def list_exported_functions(elf_file_path,fun_name):
with open(elf_file_path, 'rb') as file:
elf = ELFFile(file)
symtab = elf.get_section_by_name('.dynsym')
if not symtab:
print("No dynamic symbol table found.")
return 0
for symbol in symtab.iter_symbols():
if symbol['st_info']['type'] == 'STT_FUNC':
if symbol.name == fun_name:
print(f"Function: {symbol.name}, Address: 0x{symbol['st_value']:X}")
return symbol['st_value']
hasp_update_of = list_exported_functions(FileOrg,"hasp_update")
logging.info(f"hasp_update_of = 0x{hasp_update_of:x}")
logging.info(f"plt_dlopen_of = 0x{plt_dlopen_of:x}")
logging.info(f"hasp_login_scope_nullsub = 0x{hasp_login_scope_BL:x}")
logging.info(f"FileNameAdd = 0x{FileNameAdd:x}")
def modify_high_byte(dword, new_byte):
dword &= 0x00FFFFFF
dword |= (new_byte << 24)
return dword
with open(FileOrg, 'rb') as f:
data = f.read()
with open(FileNew, 'wb') as f:
f.write(data)
f.seek(hasp_update_of)
f.write(hasp_update_code_new)
print(f"patch hasp_update done")
BL_dlopen_of = hasp_update_of + 0x14
print(f"patch BL dlopen @ 0x{BL_dlopen_of:X}")
f.seek(BL_dlopen_of)
dwTmp = plt_dlopen_of - (BL_dlopen_of + 8)
dwTmp2 = int(dwTmp/4)
print(f"dwTmp2 {hex(dwTmp2 & 0xffffffff)}")
newByte = 0xeb
newDWORD = modify_high_byte(dwTmp2,newByte)
newCode = newDWORD.to_bytes(4,byteorder='little')
f.write(newCode)
newStrof = FileNameAdd - BL_dlopen_of + 0x0d
newStrof = newStrof & 0xFFFFFFFF
f.seek(hasp_update_of + 0x1c)
newCode = newStrof.to_bytes(4,byteorder='little')
f.write(newCode)
dwTmp = hasp_login_scope_BL + 8
dwNew2 = int((hasp_update_of - dwTmp)/4)
print(f"DWORD {hex(dwNew2 & 0xffffffff)}")
newByte = 0xeb
hasp_login_scope_BL_CODE = modify_high_byte(dwNew2,newByte)
print(f"hasp_login_scope_BL_CODE {hex(hasp_login_scope_BL_CODE & 0xffffffff)}")
f.seek(hasp_login_scope_BL)
bData = hasp_login_scope_BL_CODE.to_bytes(4,byteorder='little')
f.write(bData)
f.close()
看雪ID:sungy
https://bbs.kanxue.com/user-home-4656.htm
*本文为看雪论坛优秀文章,由 sungy 原创,转载请注明来自看雪社区




















